Cross-post of Brave fingerprinting protection not entirely foolproof - #7 by Unl0ckd
Description of the issue:
Brave Desktop fingerprinting protection not working as described.
Exact URL of the website in question:
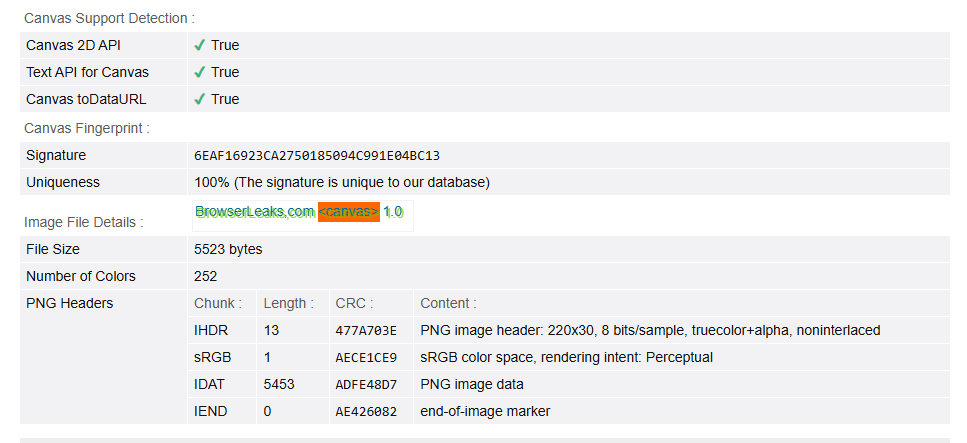
Screenshot of the ad as it appears in Brave:
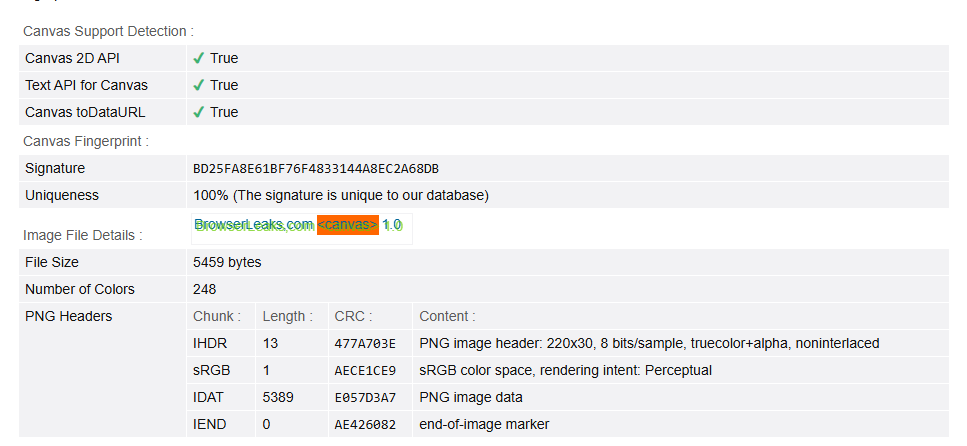
First visit:
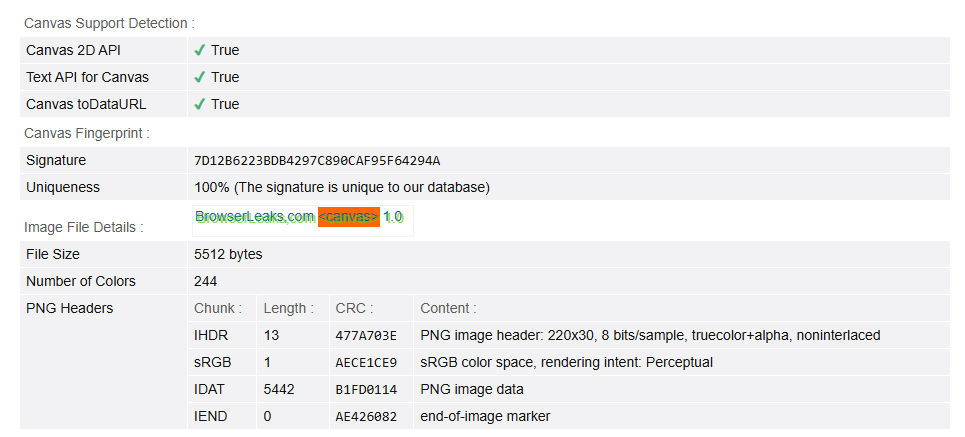
Clearing site data, closing browser, and re-opening this page:
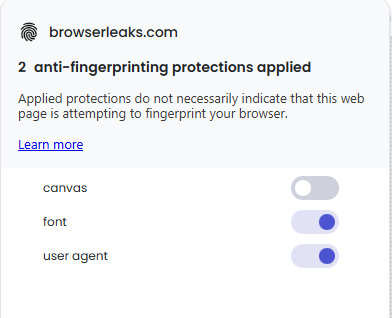
Did the issue present with default Shields settings? (yes/no)
Yes, also yes with aggressive ad and tracker blocking set
Does the site function as expected when Shields are turned off?
The fingerprint is different, but will persist through browser restarts
Does the ad appear when using a Private window as well? (yes/no)
The fingerprint is different when using a private window, but it will persist through browser restarts.
What OS are you using when you see the ad?
macOS
Brave version (check About Brave):
1.80.124
This seems like a bug because:
According to https://brave.com/privacy-updates/3-fingerprint-randomization/, the restarting the browser and visiting this site should result in a different fingerprint (emphasis below mine):
You can see these defenses at work by visiting fingerprinting demonstration websites (e.g., web audio, canvas). First, to demonstrate how fingerprinting can identify you across sessions, try the following steps in any current browser (Chrome, Firefox, Safari, Edge, or even the Tor Browser Bundle).
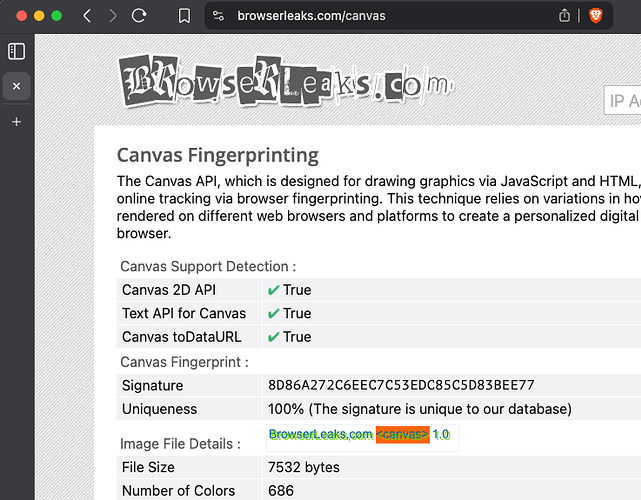
- Visit audiofingerprint.openwpm.com or browserleaks.com/canvas
- Note the fingerprinted values
- Reload the browser after clearing storage, either by deleting all browser data or opening a new private window
- Note the same fingerprint is assigned, despite all storage, cookies, etc being cleared.
This cross-storage fingerprint value is how finger-printers track you on the Web. If you now perform the same four steps in Brave Nightly, you’ll notice a different fingerprint value on each visit, demonstrating that your fingerprint cannot be used to link these two visits, and protecting your privacy. Additionally, because these fingerprinting still work the way sites expect, Brave users can still enjoy sites that use audio, canvas and WebGL for user-serving purposes, without the risk of being tracked.